link:
Web

Overview
”Web Fundamentals” provides an in-depth look at the essential technologies and protocols that form the backbone of the internet and web applications. This topic serves as a comprehensive introduction to the architecture and core components that facilitate web communication and functionality.
Content
Introduction to the Web
The web, a pivotal innovation in global communication, operates on a network of computers connected via the internet. It enables the seamless exchange of information through web applications that users interact with daily. At its core, the web uses HTTP (Hypertext Transfer Protocol) to facilitate communications, which are structured around the client-server model.
Web applications are dynamic platforms that deliver content and services to users. They run on web browsers and interact with web servers to fetch data, often using a mix of technologies like HTML, CSS, and JavaScript to create interactive experiences. Each web application operates within the framework of the client-server architecture, where the client (the user’s device) sends requests to a server that processes them and returns the requested content or data.
For a more detailed understanding of how these interactions are structured, see Client-Server Architecture Pattern.
This structure not only simplifies the interaction between disparate computing devices but also underpins the functionality of the internet, allowing for scalable, distributed, and flexible communication pathways. This connectivity is essential for the vast array of online activities, from simple browsing and shopping to complex cloud-based applications and services
Connection to OSI model
The OSI (Open Systems Interconnection) model provides a layered framework that explains the different stages data goes through from physical transmission to application processing on the web. This structured approach helps clarify how various networking technologies interact to deliver web services. For an in-depth look at each layer’s role in web communications, see OSI model.
Web Communication Protocols
Content
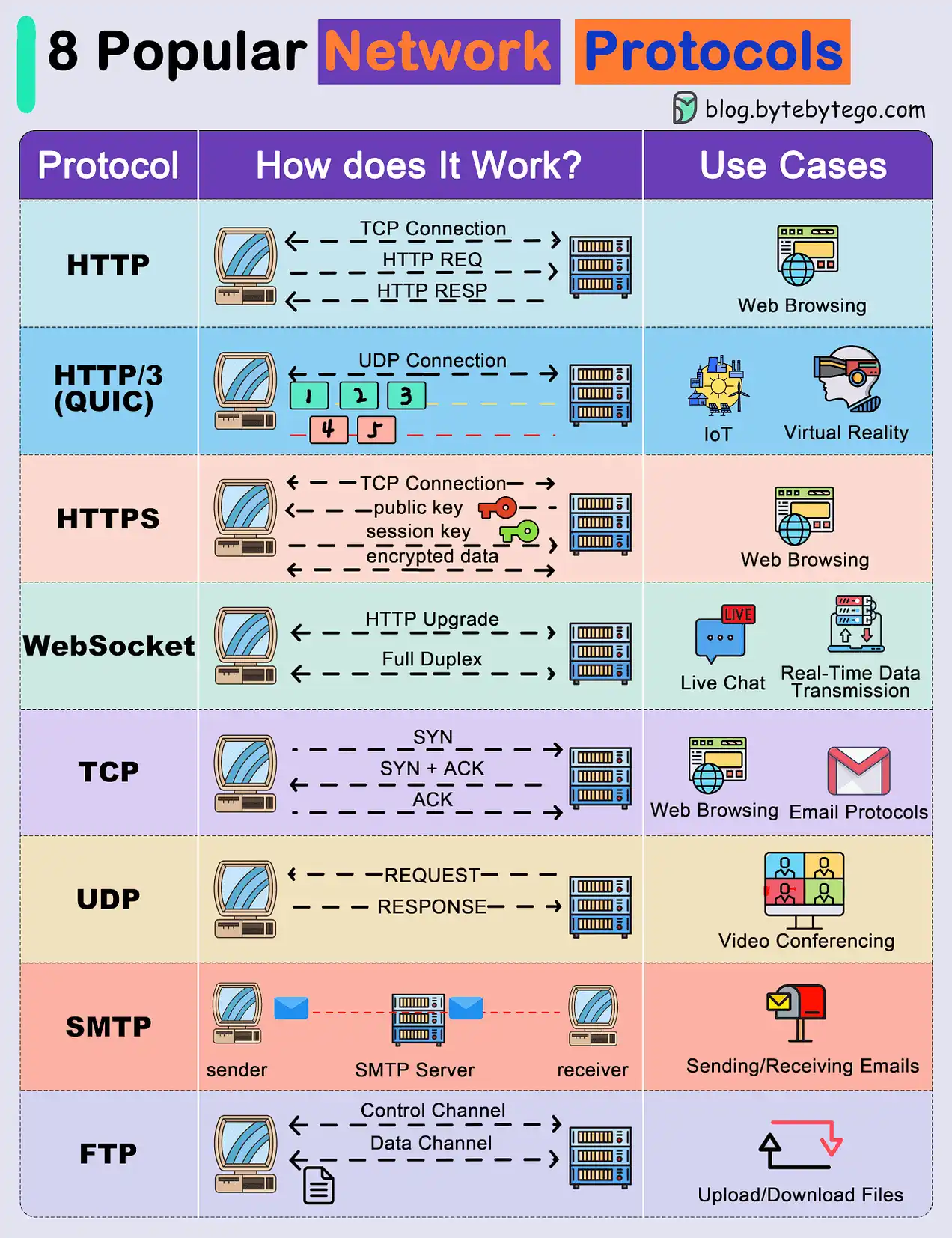
HTTP and Its Evolutions
The Hypertext Transfer Protocol (HTTP) and its subsequent versions are central to web data exchange, forming the basis of data communication on the World Wide Web.
Overview
HTTP, or Hypertext Transfer Protocol, has seen several iterations, each bringing advancements in performance, security, and functionality. Here’s a brief overview of key versions:
HTTP 1.1: Introduced persistent connections, pipelining, and chunked transfer encoding, enhancing efficiency.
HTTP 2.0: Introduced multiplexing, header compression, and server push, significantly improving speed and performance.
HTTP 3.0: Utilizes the QUIC Protocol transport protocol over UDP for reduced latency and improved security compared to TCP-based protocols.
HTTPS: Not a separate version but an extension that adds encryption to HTTP, ensuring secure data transmission over the internet.
Understanding these versions and their differences is essential for optimizing web performance and ensuring secure communication between clients and servers.
Link to originalVersion Comparison
Feature HTTP 1.0 HTTP 1.1 HTTP/2 HTTP/3 Multiplexing No No Yes Yes Header Compression No No Yes Yes Server Push No No Yes Yes (with server support) Persistent Connections No Yes Yes Yes Connection Reuse No Yes Yes Yes Stream Prioritization No No Yes Yes Encryption No No Yes (over TLS) Yes (over [[QUIC Protocol Latency Higher Lower Lower Lower Protocol HTTP HTTP Binary framing layer over TCP/TLS Datagram-based protocol over UDP Overhead Higher Lower Lower Lower Compatibility Older Widely used Widely supported Emerging Transmission Protocols
Transmission protocols like TCP and UDP play critical roles in how data is sent and received over the network.
- TCP vs UDP: Discusses the differences between TCP, a connection-oriented protocol that ensures reliable and ordered delivery, and UDP, which is faster but does not guarantee delivery or order, making it suitable for applications where speed is crucial.
Additional Protocols
This section explores other essential protocols used in various aspects of internet communications:
- IP: The fundamental protocol for sending data across the internet, IP is responsible for addressing and routing packets of data so they can travel across networks and arrive at the correct destination.
- Domain Name System (DNS): Translates domain names into IP addresses, allowing users to access websites using familiar names instead of numerical IP addresses.
- SSL and TLS Protocols: Protocols that secure communications over computer networks, widely used for web browsing, email, and other data transfer applications.
- WebSockets: Enables real-time communication between user browsers and web servers, which is particularly useful for live messaging and gaming applications.
- Content Delivery Networks (CDNs): Networks of servers that work together to distribute web content efficiently to users based on their geographic location, improving site speed and reducing latency.
Email Protocols
Email communication is governed by several protocols that manage the transmission and reception of email messages:
- SMTP: The protocol for sending email messages from a client to a server and between servers.
- IMAP and POP3: Protocols used for retrieving emails from a server, with IMAP offering more complex management features compared to POP3.
File Transfer Protocols
These protocols are designed for secure data transfer, especially in environments that require confidentiality and data integrity:
- File Transfer Protocol (FTP): Enables the transfer of files between a client and a server on a network.
- SSH File Transfer Protocol (SFTP): Part of the SSH Protocol suite that provides secure file transfer capabilities.
Link to original
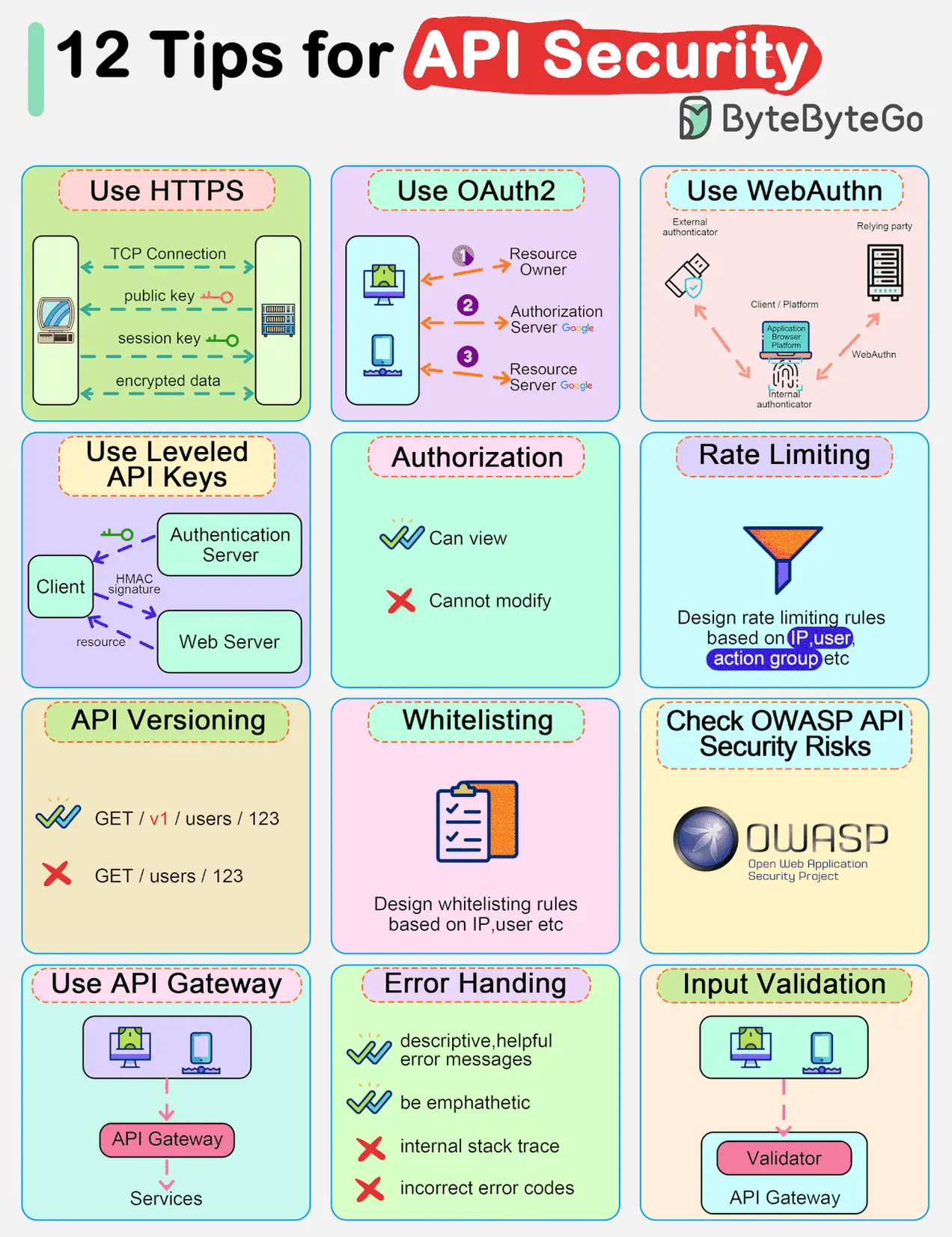
Web Security
Web Security
Diagram
Overview
Security in Web and API development involves implementing measures to protect data, communications, and resources from unauthorized access and attacks. This note consolidates key security concepts, strategies, and tools essential for safeguarding web applications and APIs.
Content
Encryption and Data Protection
- End-to-End Encryption: Ensures data sent between two parties cannot be intercepted or tampered with, providing confidentiality and integrity.
- SSL and TLS Protocols: Secure internet communications by encrypting data exchanged over the web, essential for web browsing, email, and more.
- Data Cryptography: Secures data by transforming it into a format that cannot be easily understood by unauthorized users, using cryptographic algorithms and keys.
Network and Communication Security
- VPN: Virtual Private Networks secure and encrypt connections over less secure networks like the internet, protecting sensitive data and user identities.
- IPSec (Internet Protocol Security): A suite of protocols used to secure Internet communications by authenticating and encrypting each IP packet of a communication session.
- SSH (Secure Shell): Provides a secure channel over an unsecured network, offering strong authentication and encrypted data communications between two computers.
Authentication and Authorization
- Authentication: Techniques that ensure only authorized users can access a network or a resource, including methods like passwords, biometrics, two-factor authentication (2FA), and digital certificates.
- Authorization: The process of granting or denying specific permissions to users, groups, or roles to access resources or perform operations within a network or application environment.
- SSO (Single Sign-On): Allows users to authenticate once and gain access to multiple systems without re-entering credentials.
- Access Control Lists: Define which users can access which resources, providing a fine-grained security control.
Token-Based Authentication
- JSON Web Tokens (JWT): A method for securely transmitting information as a JSON object.
- OAuth 2.0: A protocol for authorization, providing a secure delegated access to server resources.
- OAuth 2.0 Flows: Different authentication flows for varying application scenarios.
- OAuth PKCE: Enhancement for public clients on mobile or desktop applications.
- OpenID Connect: An identity layer on top of OAuth 2.0 for authentication.
Security Protocols and Practices
- TLS: Protocols for securing communications over a computer network.
- Cross-Origin Resource Sharing: A mechanism that allows or restricts requested resources on a web server depending on where the HTTP request was initiated.
Threat Detection and Management
- Intrusion Detection Systems: Detects unauthorized access or anomalies in API usage.
- Rate Limiting: Prevents abuse and ensures fair use by limiting how often each user can call the API.
- Web Application Firewalls (WAF): Protects web applications from attacks by filtering and monitoring HTTP traffic, effective against threats like XSS and SQL injection.
Compliance and Best Practices
- OWASP API Security: Check for more recommendations and cheatsheets from OWASP.
- API Gateway Security: Uses gateways as an additional layer of security to enforce API policies and reduce the risk of attacks.
- Software Testing: Regular penetration testing, vulnerability assessments, and security audits to identify and mitigate risks.
- IPv4 vs IPv6: Details the functionalities and improvements brought by IPv6 over IPv4, enhancing security capabilities and simplifying network configuration.
Conclusion
Consolidating web and API security into a unified approach provides a comprehensive understanding of the measures required to protect applications and data. By implementing robust encryption, network security, access control, and threat management strategies, developers can ensure the security and integrity of their systems.
Link to original
Web Data Handling and Formats
Web Data Handling and Formats
Data Formats
Data formats are crucial for structuring the data that is exchanged between web clients and servers. Here are two of the most widely used data formats:
- XML: A flexible text format that defines a set of rules for encoding documents in a format that is both human-readable and machine-readable. Widely used in complex data structures across various web technologies.
- JSON: Lightweight data-interchange format that is easy for humans to read and write, and easy for machines to parse and generate. Predominantly used in web applications as it is natively supported by JavaScript.
- Protobuf: Compared to JSON, which uses text, Protobuf’s binary format significantly reduces payload size, enhancing both transmission speed and efficiency.
MIME Types
MIME types play a crucial role in the web by specifying the nature and format of a file. They are used to determine how a file should be processed by a browser.
- MIME types are a standard way of classifying file types on the Internet. They are used in web communications to inform the browser about the type of the file being sent, helping the browser to display or handle the file appropriately.
Link to originalCommon Character Encodings:
- UTF-8: A character encoding capable of encoding all possible characters (called code points) in Unicode. It is the dominant character encoding for the internet.
- ASCII (American Standard Code for Information Interchange): An older character encoding standard that encodes 128 specified characters into seven-bit integers.
Session Management
Session Management
- Cookies and Session Management: Overview of how web applications maintain user state and session information using cookies and other session management techniques.