link: Web Security
Access Control Lists (ACLs)
Overview
Access Control Lists (ACLs) are a security mechanism used to define and manage the permissions granted to various users, groups, or systems for accessing specific resources within a computing environment. ACLs provide a fine-grained control over who can perform what actions on resources, enhancing security and ensuring that only authorized entities have the necessary access.
Key Concepts
Important
- Access Control Entry (ACE): An individual entry in an ACL that defines the permissions for a specific user or group.
- Permissions: The specific actions that are allowed or denied by an ACE, such as read, write, execute, or delete.
- Resource: Any object that can be accessed, such as files, directories, network devices, or applications.
- DACL (Discretionary ACL): Specifies the access rights granted or denied to users and groups.
- SACL (System ACL): Used to specify the actions that should be audited when performed by a user or group.
Types of ACLs
Summary
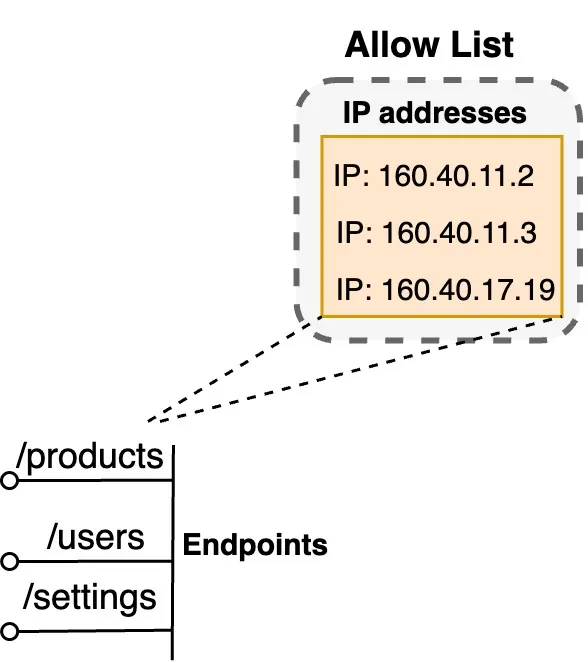
- Standard ACLs: Basic ACLs that allow or deny traffic based on source IP addresses. These are simpler and have limited criteria for filtering.
- Extended ACLs: More advanced ACLs that provide greater control by allowing or denying traffic based on multiple criteria, including source and destination IP addresses, protocol types, and port numbers.
- File System ACLs: Control access to files and directories on a file system.
- Network ACLs: Manage access to network devices, routers, and switches.
- Database ACLs: Define access permissions for database objects such as tables, views, and procedures.
- Application ACLs: Control access to application resources and functionalities.
How It Works
Summary
- Define ACLs: ACLs are defined and associated with resources, specifying which users or groups have what types of access.
- Access Request: When a user attempts to access a resource, the system checks the ACL associated with that resource.
- Evaluate ACEs: The system evaluates each Access Control Entry (ACE) in the ACL to determine if the requested access should be allowed or denied.
- Grant or Deny Access: Based on the evaluation of ACEs, the system either grants or denies access to the resource.
- Log Actions (SACL): If a System ACL (SACL) is in place, the action (whether granted or denied) may be logged for auditing purposes.
Best Use Cases
- File System Security: Implementing ACLs to control access to sensitive files and directories.
- Network Security: Using network ACLs to regulate traffic flow and restrict access to network devices.
- Database Security: Applying ACLs to databases to control access to data and ensure only authorized users can perform certain operations.
- Application Security: Using ACLs within applications to manage user permissions and access to different functionalities.
- Cloud Environments: Utilizing AWS SG, Azure NSG , and Firewall Rules (Google Cloud) to manage and secure access to cloud resources.
Related Topics
Summary
- Authentication: Ensures that only authorized users can access a system or resource. ACLs work in conjunction with authentication mechanisms to verify the identity of users before checking their permissions.
- Authorization: Determines what authenticated users are allowed to do. ACLs are a key component of the authorization process, specifying the actions permitted for different users or groups.
- Role-Based Access Control: A method of restricting access based on roles assigned to users. While ACLs specify permissions for individual users or groups, RBAC assigns permissions to roles, which are then assigned to users. Both can be used together to enhance security.
Conclusion
Access Control Lists (ACLs) are a critical component of a robust security strategy, offering fine-grained control over who can access resources and what actions they can perform. By implementing and managing ACLs effectively, organizations can enhance security, ensure compliance, and protect sensitive data and systems from unauthorized access.