link: Web Security
Authentication
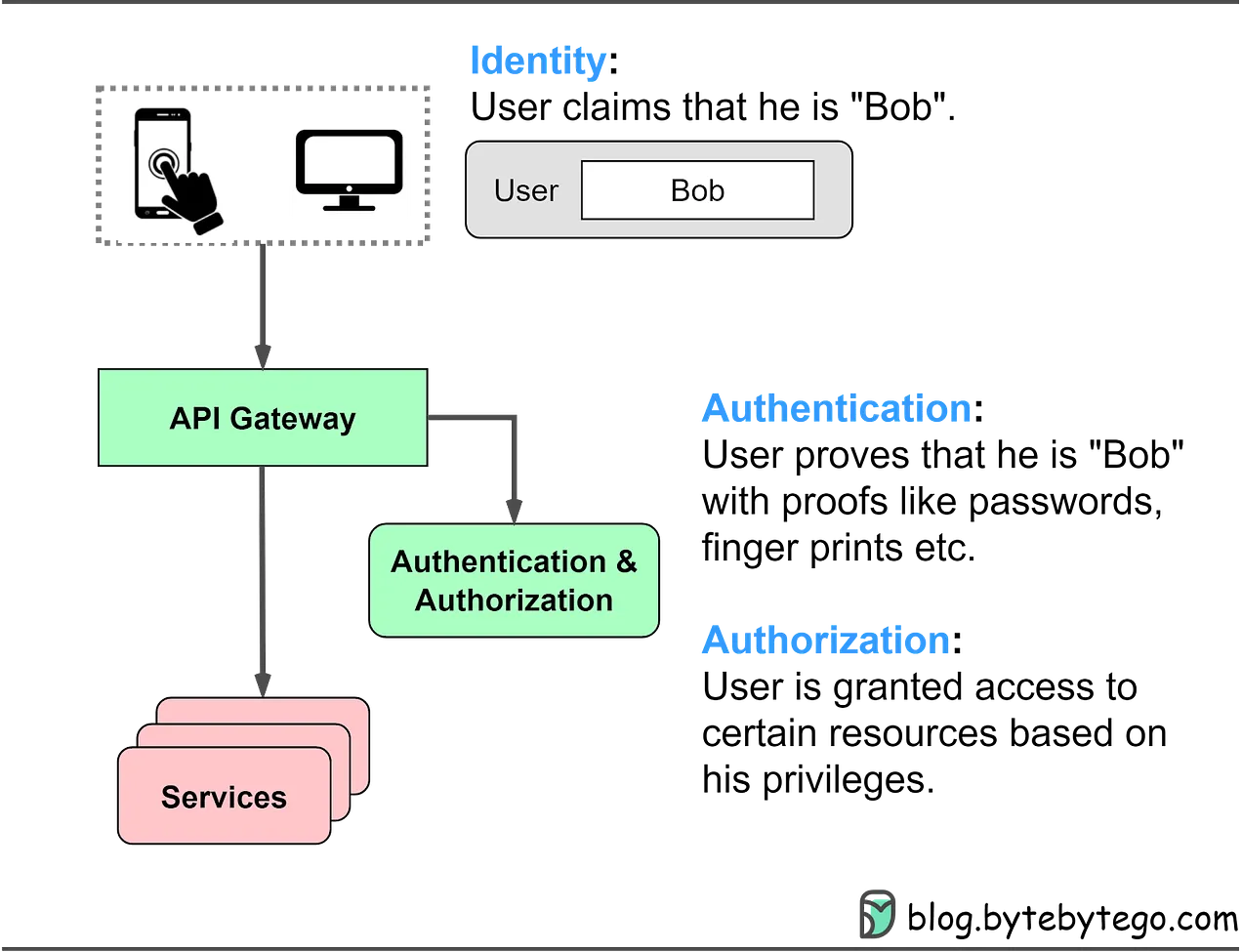
Overview
Authentication is the process of verifying the identity of a user or system. It ensures that users are who they claim to be, which is a fundamental aspect of securing web applications and systems.
Importance of Authentication
Authentication is crucial for securing access to systems and applications, ensuring that only authorized users can access sensitive information. It helps prevent unauthorized access, data breaches, and other security threats.
Important
- Security: Protects sensitive data and systems from unauthorized access.
- Data Integrity: Ensures that data remains accurate and unaltered.
- Accountability: Tracks user actions, ensuring that activities can be traced back to authenticated users.
- User Trust: Enhances user confidence by protecting personal information.
Authentication Methods
Various methods are employed to authenticate users and systems. These methods range from simple password-based authentication to more complex multi-factor authentication.
Summary
- Password-Based Authentication: Traditional method using a combination of username and password.
- HTTP Basic Authentication: Simple method for passing credentials.
- Session-Cookie Authentication: Uses cookies to maintain a session state.
- Token-Based Authentication: Utilizes tokens for session management (e.g., JWT).
- Passwordless Authentication: Eliminates the need for passwords by using alternative methods.
- Email Link Authentication: Authentication via links sent to email.
- SMS or Email OTP: One-time passwords sent via SMS or email.
- Biometric Authentication: Uses biometrics such as fingerprints or facial recognition.
- Push Notification Authentication: Uses push notifications for authentication.
- Hardware Token Authentication: Utilizes hardware tokens for authentication.
- Multi-Factor Authentication (MFA): Combines multiple authentication methods to enhance security.
- Single Sign-On (SSO): Allows users to authenticate once and gain access to multiple systems.
- OAuth 2.0: Authorization framework for third-party applications.
- OpenID Connect: Identity layer on top of OAuth 2.0 for authentication.
How Authentication Works
Authentication Process
- User Request: The user attempts to access a system or application.
- Credentials Submission: The user provides credentials (e.g., username and password).
- Verification: The system verifies the credentials against stored information.
- Access Granted: If the credentials are valid, the user is granted access.
- Session Management: The system manages the user’s session, typically using tokens or cookies to maintain authentication state.
Best Practices for Authentication
Implementing best practices for authentication can significantly enhance security. Some key practices include:
Authentication Best Practices
- Use Strong Passwords: Enforce strong password policies to ensure complexity.
- Implement MFA: Use multi-factor authentication to add an extra layer of security.
- Secure Token Storage: Ensure tokens are securely stored and transmitted.
- Regularly Update Security Measures: Keep authentication mechanisms up-to-date with the latest security standards.
- Monitor and Audit: Regularly monitor and audit authentication logs for suspicious activities.
Related Topics
Summary
- Authorization: Determines what authenticated users are allowed to do. It works hand-in-hand with authentication to ensure secure access control.
- Identity Management: Manages user identities and access privileges, often integrating with authentication systems.
- Access Control Lists (ACLs): Defines permissions for users and systems, controlling what authenticated users can do.
- Security Policies: Establishes rules and practices for secure authentication and access control.
- Encryption: Protects data in transit and at rest, ensuring that authentication data is securely transmitted and stored.
- OAuth 2.0: An authorization framework that complements authentication methods, enabling secure API access.
- Zero Trust Security: A security model that requires strict identity verification for every person and device attempting to access resources.
Conclusion
Authentication is a critical aspect of web security, providing the foundation for protecting sensitive information and ensuring that only authorized users have access to systems and applications. By understanding and implementing various authentication methods and best practices, organizations can enhance their security posture and protect their digital assets.
References
What Is API Authentication? Benefits, Methods & Best Practices | Postman