link: Password-Based Authentication ,Session Management
Web Tokens
Overview
Web tokens are a mechanism used in web development for securely transmitting information between parties. They are commonly used for Authentication, Authorization, and information exchange. Web tokens can encapsulate various types of claims and metadata, making them versatile tools for ensuring secure and efficient communication in Web applications.
Token-Based Authentication
Token-based authentication is a modern approach to secure user access in web applications and native mobile apps. It addresses some limitations of Session-Cookie Authentication and offers advantages such as stateless server-side handling and better compatibility with various platforms.
Types of Web Tokens
There are several types of web tokens, each with unique features and use cases:
Types of Web Tokens
- Json Web Tokens (JWT): A compact, URL-safe token format that is widely used for authentication and authorization. JWTs contain three parts: a header, a payload, and a signature, and are designed to be self-contained and stateless.
- Security Assertion Markup Language (SAML) Tokens: XML-based tokens used primarily for single sign-on (SSO) in enterprise environments. SAML tokens facilitate the exchange of authentication and authorization data between parties.
- OAuth Tokens: Tokens used in the OAuth 2.0 framework to grant access to resources without sharing user credentials. OAuth tokens can be in the form of access tokens, refresh tokens, or ID tokens (when used with OpenID Connect).
- Simple Web Tokens (SWT): A lightweight token format used for authentication and authorization, often replaced by JWTs in modern applications due to the latter’s enhanced features.
How Web Tokens Work
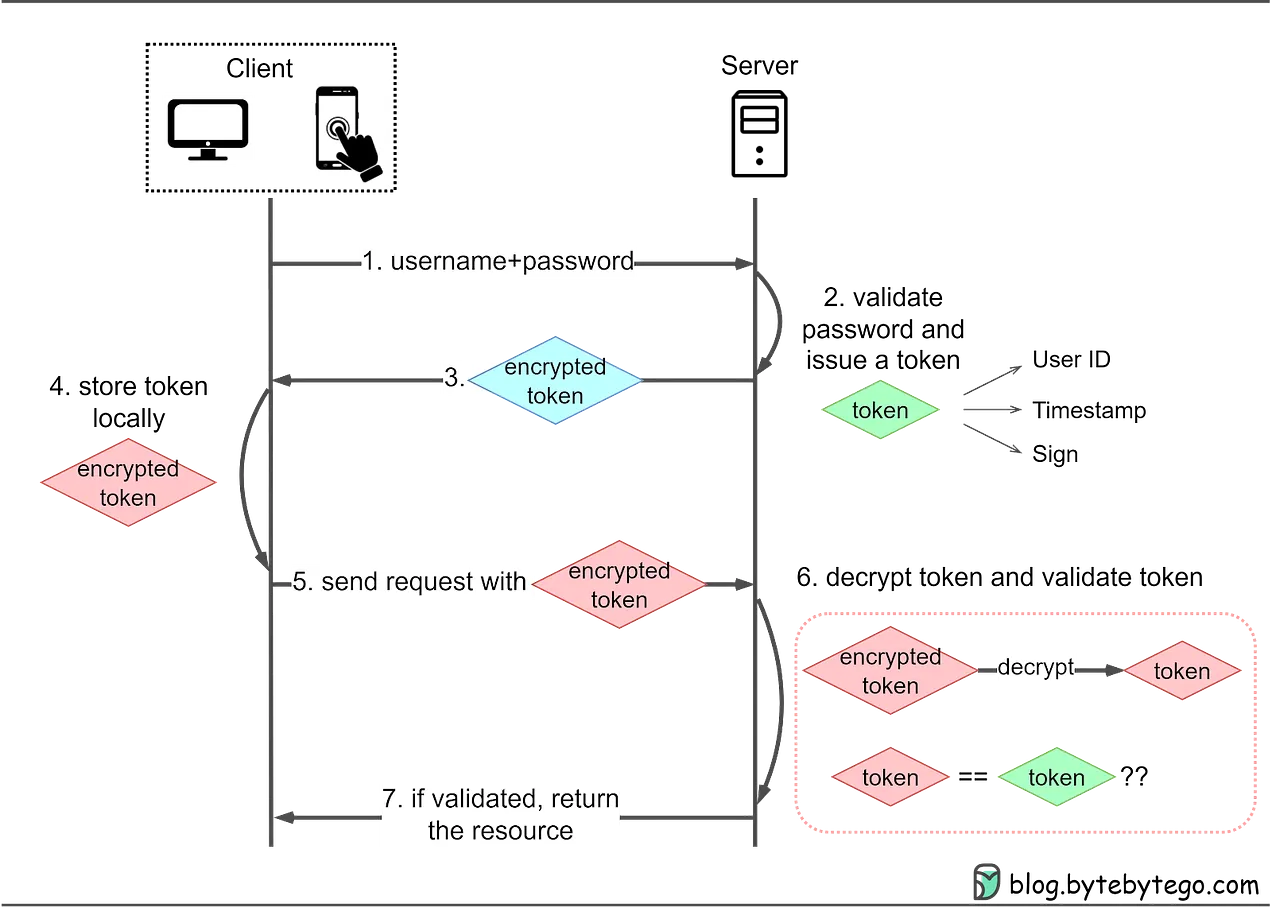
How Web Tokens Work
The client sends a request to access a protected resource on the server. If the client hasn’t yet authenticated, the server responds with a login prompt. The client submits their username and password to the server.
The server verifies the provided credentials and, if valid, issues a unique token.
The token is sent back to the client.
The client stores the token in local storage.
Subsequent requests include the token in the HTTP header.
The server validates the received token.
The server grants access to the requested resource.
Pros/Cons
Pros
- Stateless Authentication: Web tokens enable stateless authentication, improving scalability and reducing server load.
- Compact and URL-Safe: Tokens are small and can be easily transmitted via URLs, POST parameters, or HTTP headers.
- Interoperability: Web tokens can be used across different platforms and technologies, facilitating seamless integration.
- Security: Properly implemented tokens ensure secure communication by encapsulating authentication and authorization data.
Cons
- Security Risks: Storing sensitive information in tokens can be risky. Always encrypt sensitive data and validate tokens on the server side.
- Token Revocation: Revoking tokens can be challenging, especially with stateless tokens like JWTs.
- Complexity: Implementing secure token management and handling can add complexity to the application.
Use Cases
Use Cases
- Authentication: Tokens are commonly used for user authentication in web and mobile applications.
- Authorization: Tokens help control access to resources, ensuring only authorized users can perform specific actions.
- Information Exchange: Securely transmitting information between parties in a compact and standardized format.