link:
API (Application Programming Interface)
Overview
APIs, or Application Programming Interfaces, establish guidelines for how software programs interact, crucial for exchanging data and functions across different systems. These interfaces are vital for creating interconnected experiences on Web, mobile, and cloud platforms, forming a fundamental part of modern software development.
Important
The approach known as API-First emphasizes designing APIs at the beginning of a project. This strategy prioritizes API development to enhance integration and scalability of systems, facilitating a streamlined and efficient development process.
Introduction
APIs simplify complex software interactions by defining accessible methods and data formats for applications. This abstraction allows developers to use predefined functionalities to enhance application interoperability across various platforms and devices, fostering a more integrated digital environment.
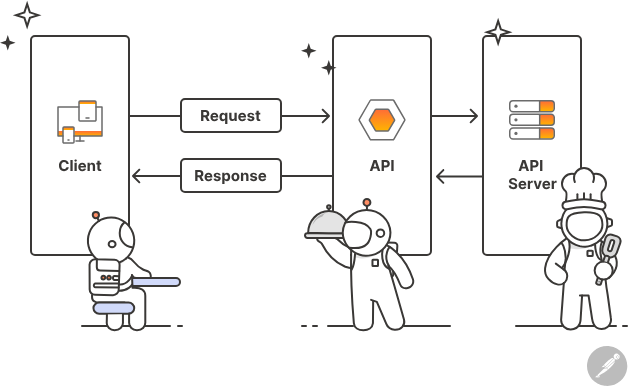
How Do APIs Work?
Similar to a restaurant’s service workflow, where the waiter (API) communicates your order (request) to the kitchen (system) to prepare your meal (data/response), APIs operate on a request-response model. They help streamline processes by ensuring that applications can request and receive data efficiently and securely.
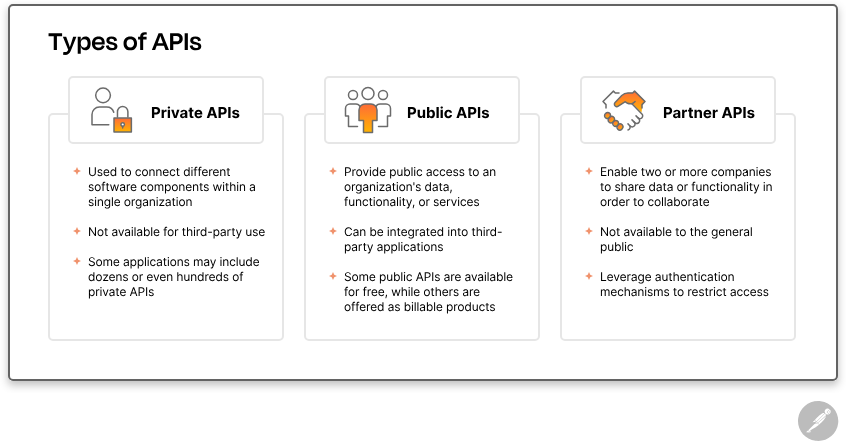
Types and Architectures of APIs
APIs can be broadly categorized by accessibility or by their architectural design, each suited to different use cases.
API Accessibility
- Private APIs: These are internally used by organizations to enhance their technological frameworks and streamline internal functionalities.
- Public APIs: Open to external developers, these APIs widen an application’s reach and foster external innovation.
- Partner APIs: Shared exclusively with business allies, these APIs facilitate specific integrative functions between allied entities.
API Architectures
API Architectural Styles
API architectural styles are designed to suit specific scenarios and requirements, each offering unique advantages:
API Architectural Styles
- REST API: Emphasizes simplicity and statelessness, leveraging standard HTTP methods. REST is highly scalable and flexible, making it ideal for general web services.
- SOAP API: Utilizes XML for structured data exchange, with strict standards that enhance security, suitable for enterprise-level applications.
- GraphQL API: Enables clients to precisely define the data they need, reducing the number of requests and improving efficiencies in dynamic web applications.
- Webhooks API: Facilitates real-time data push through HTTP callbacks, ideal for applications that require instant updates.
- WebSockets: Establishes a full-duplex communication channel that remains open, allowing real-time, bi-directional interactions over a single TCP between client and server. Ideal for features like live chat and online gaming.
- gRPC API: Uses HTTP 2.0 and Protobuf for efficient, high-performance communication in microservices architectures, supporting advanced features like streaming.
Comparison
Feature REST API SOAP API GraphQL API Webhooks API WebSockets gRPC API Communication Type Stateless Stateful Stateless Event-driven Full-duplex Full-duplex Protocol HTTP HTTP HTTP HTTP TCP HTTP 2.0 Characteristics Simple, flexible, uses standard HTTP methods Strict standards, uses XML, high security Allows clients to request exactly what they need Uses callbacks to deliver data in real time Maintains a persistent connection for real-time, bidirectional communication Efficient, low-latency, supports streaming Scalability High Moderate High Depends on implementation High High Security Level Moderate High Moderate Moderate Moderate High Typical Use Cases General web services, mobile apps, social networks Enterprise applications, financial services, complex transactions Dynamic web apps, real-time data fetching Automating workflows, real-time updates Live chat, online gaming, collaborative environments Microservices, high-performance internal services Link to originalKey Insights
- Communication Type: Reflects how data is managed between client and server, with stateless systems like REST and GraphQL not maintaining any server state, unlike stateful systems like SOAP.
- Scalability: Highlights the architecture’s ability to handle increases in users or data volume. REST, GraphQL, and gRPC excel due to their efficient handling of requests and connections.
- Security Level: Some architectures, such as SOAP and gRPC, offer more robust security features crucial for managing sensitive or critical data.
- Typical Use Cases: Each API style is optimal for specific scenarios, from general web services (REST) to complex financial transactions (SOAP) and real-time interactive applications (Websockets, gRPC).
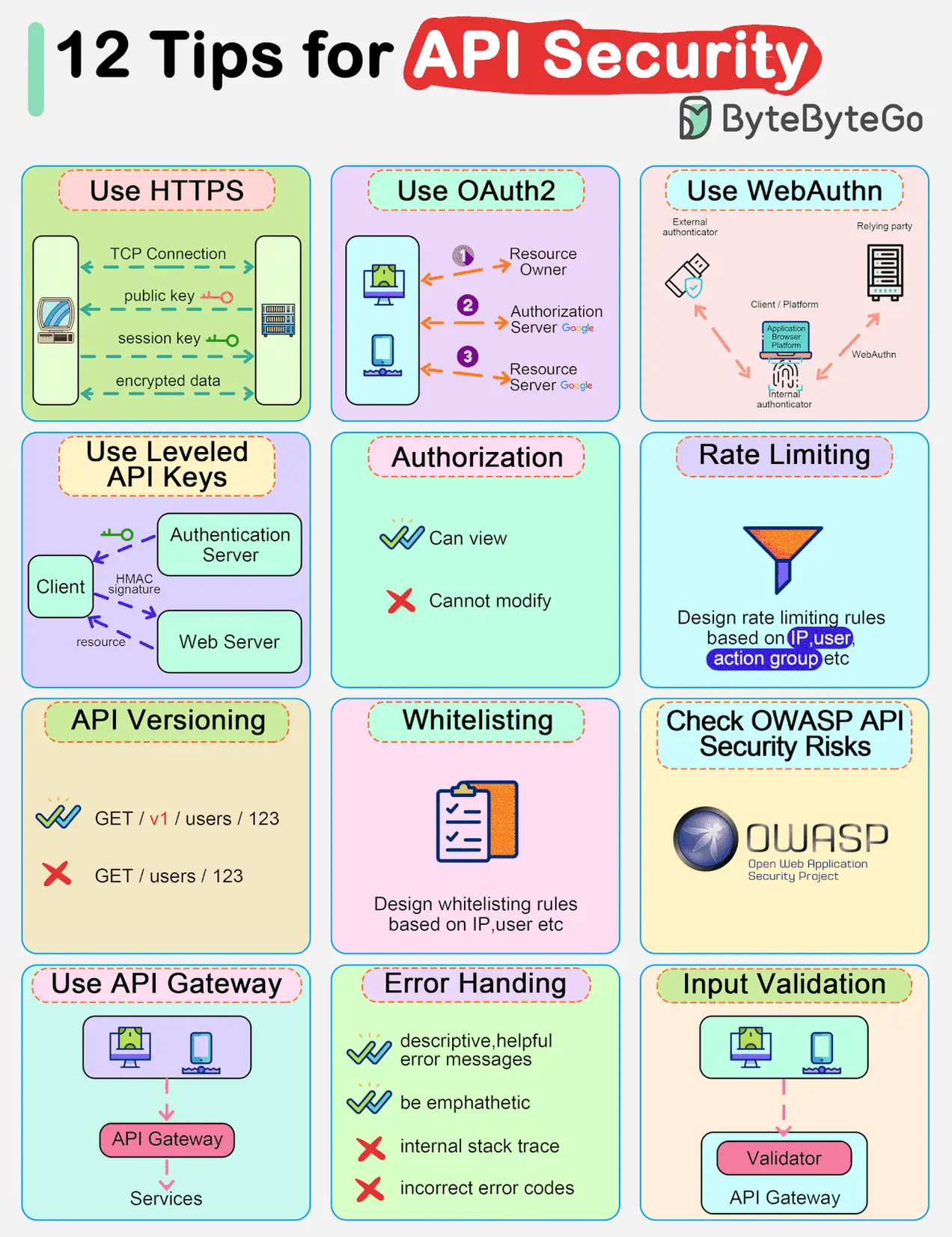
Web Security
Diagram
Link to original
Content
Encryption and Data Protection
- End-to-End Encryption: Ensures data sent between two parties cannot be intercepted or tampered with, providing confidentiality and integrity.
- SSL and TLS Protocols: Secure internet communications by encrypting data exchanged over the web, essential for web browsing, email, and more.
- Data Cryptography: Secures data by transforming it into a format that cannot be easily understood by unauthorized users, using cryptographic algorithms and keys.
Network and Communication Security
- VPN: Virtual Private Networks secure and encrypt connections over less secure networks like the internet, protecting sensitive data and user identities.
- IPSec (Internet Protocol Security): A suite of protocols used to secure Internet communications by authenticating and encrypting each IP packet of a communication session.
- SSH (Secure Shell): Provides a secure channel over an unsecured network, offering strong authentication and encrypted data communications between two computers.
Authentication and Authorization
- Authentication: Techniques that ensure only authorized users can access a network or a resource, including methods like passwords, biometrics, two-factor authentication (2FA), and digital certificates.
- Authorization: The process of granting or denying specific permissions to users, groups, or roles to access resources or perform operations within a network or application environment.
- SSO (Single Sign-On): Allows users to authenticate once and gain access to multiple systems without re-entering credentials.
- Access Control Lists: Define which users can access which resources, providing a fine-grained security control.
Token-Based Authentication
- JSON Web Tokens (JWT): A method for securely transmitting information as a JSON object.
- OAuth 2.0: A protocol for authorization, providing a secure delegated access to server resources.
- OAuth 2.0 Flows: Different authentication flows for varying application scenarios.
- OAuth PKCE: Enhancement for public clients on mobile or desktop applications.
- OpenID Connect: An identity layer on top of OAuth 2.0 for authentication.
Security Protocols and Practices
- TLS: Protocols for securing communications over a computer network.
- Cross-Origin Resource Sharing: A mechanism that allows or restricts requested resources on a web server depending on where the HTTP request was initiated.
Threat Detection and Management
- Intrusion Detection Systems: Detects unauthorized access or anomalies in API usage.
- Rate Limiting: Prevents abuse and ensures fair use by limiting how often each user can call the API.
- Web Application Firewalls (WAF): Protects web applications from attacks by filtering and monitoring HTTP traffic, effective against threats like XSS and SQL injection.
Link to originalCompliance and Best Practices
- OWASP API Security: Check for more recommendations and cheatsheets from OWASP.
- API Gateway Security: Uses gateways as an additional layer of security to enforce API policies and reduce the risk of attacks.
- Software Testing: Regular penetration testing, vulnerability assessments, and security audits to identify and mitigate risks.
- IPv4 vs IPv6: Details the functionalities and improvements brought by IPv6 over IPv4, enhancing security capabilities and simplifying network configuration.
References
What is an API? A Beginner’s Guide to APIs | Postman Mastering the Art of API Design - by Alex Xu